How do supply chain attacks happen?
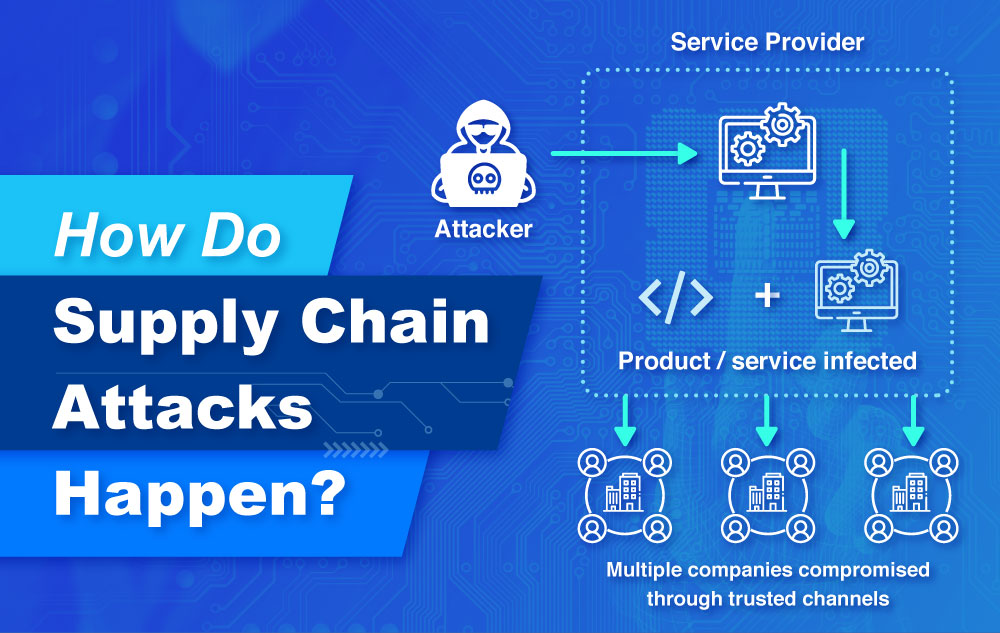
There has been an increase Supply Chain attacks in Asia-Pacific and the rest of the world as cyber threat actors seek to exploit the weakest connections in commercial and digital supply chains. These attackers infect legitimate applications to distribute malware with the purpose of gaining access to source codes, build processes, and update mechanisms.
According to Accenture, 40% of the cyberattacks in 2020 originated from the extended supply chain and is projected to multiply in the following years.
1. Vendor Compromise
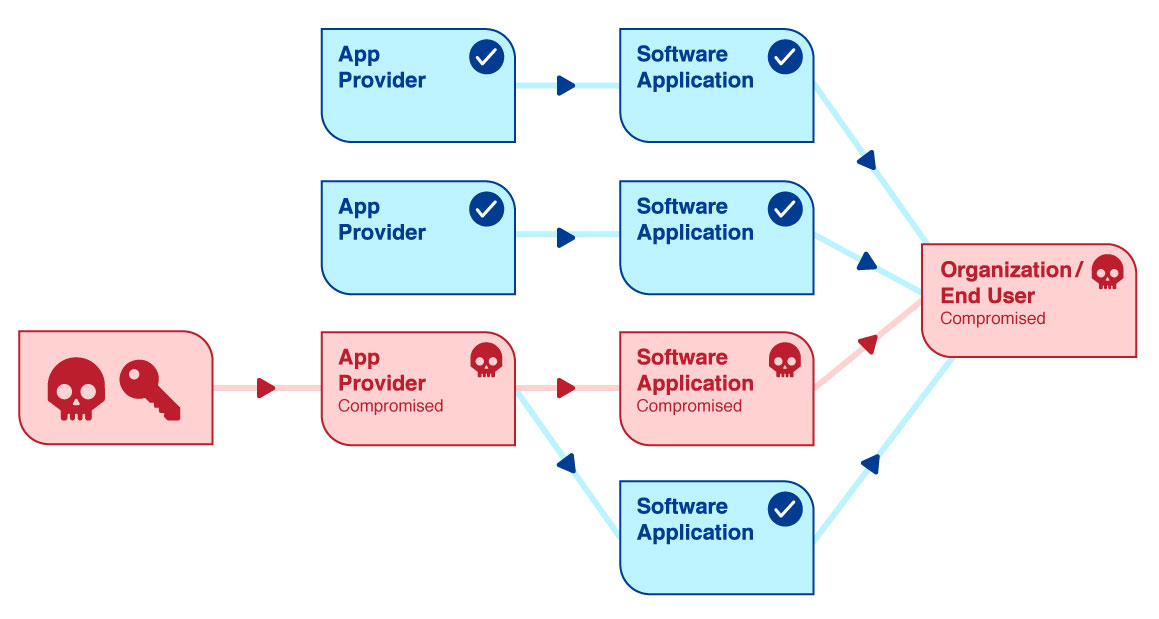
A Vendor Compromise commonly begins with the reconnaissance phase. This is where the perpetrator gathers information to determine which are the businesses that utilize the vendor’s software, the various locations that it has been installed, and the types of data, privileges, and systems that it may have access to. The next step would be to use social engineering, phishing, or other technological methods in an attempt to obtain authentic vendor employee credentials. After acquiring a foothold in the vendor’s infrastructure, the malicious actor will then try to migrate laterally to the software build environment. This will allow the attacker to alter source code of the application that the vendor supplies to its clients.
2. Third-party Software Providers Attack
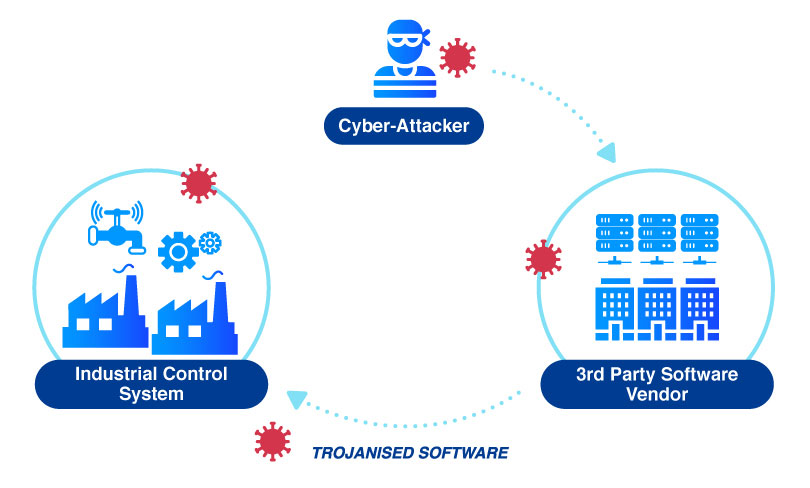
Attacks targeting “zero-days,” or unpatched security bugs, in commonly used third-party applications are another example of the risks we assume from our software supply chain. The rapid-fire ability of bad actors to take advantage of software vulnerability disclosures and our own justifiably cautious patch processes create an asymmetry with predictable results. It’s rare that an organization will be able to deploy a vendor patch the moment it is made available across all of the necessary locations.
Another example of the risks that organizations assume from your software supply chain are the attacks which target “zero-day” vulnerabilities, or unpatched security issues in widely used third-party applications. The capacity of bad actors to rapidly exploit software vulnerability disclosures, along with the understandably cautious patching processes of businesses, produces an asymmetry with predictable outcomes. It is uncommon for an organization to have the ability to install a vendor patch across all of the relevant sites the instant that the patch becomes available.
3. Website Builders Attack
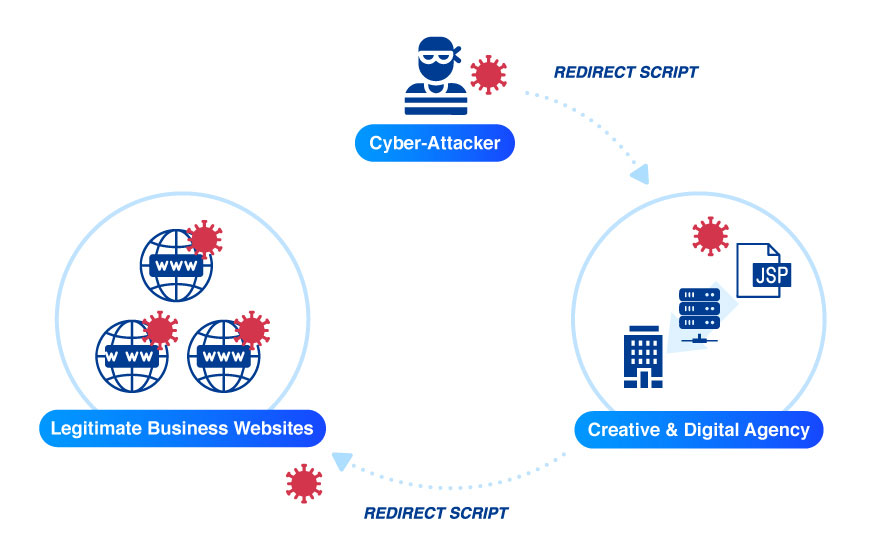
Attacks targeting “zero-days,” or unpatched security bugs, in commonly used third-party applications are another example of the risks we assume from our software supply chain. The rapid-fire ability of bad actors to take advantage of software vulnerability disclosures and our own justifiably cautious patch processes create an asymmetry with predictable results. It’s rare that an organization will be able to deploy a vendor patch the moment it is made available across all of the necessary locations.
Another example of the risks that organizations assume from your software supply chain are the attacks which target “zero-day” vulnerabilities, or unpatched security issues in widely used third-party applications. The capacity of bad actors to rapidly exploit software vulnerability disclosures, along with the understandably cautious patching processes of businesses, produces an asymmetry with predictable outcomes. It is uncommon for an organization to have the ability to install a vendor patch across all of the relevant sites the instant that the patch becomes available.
4. Dependency Confusion
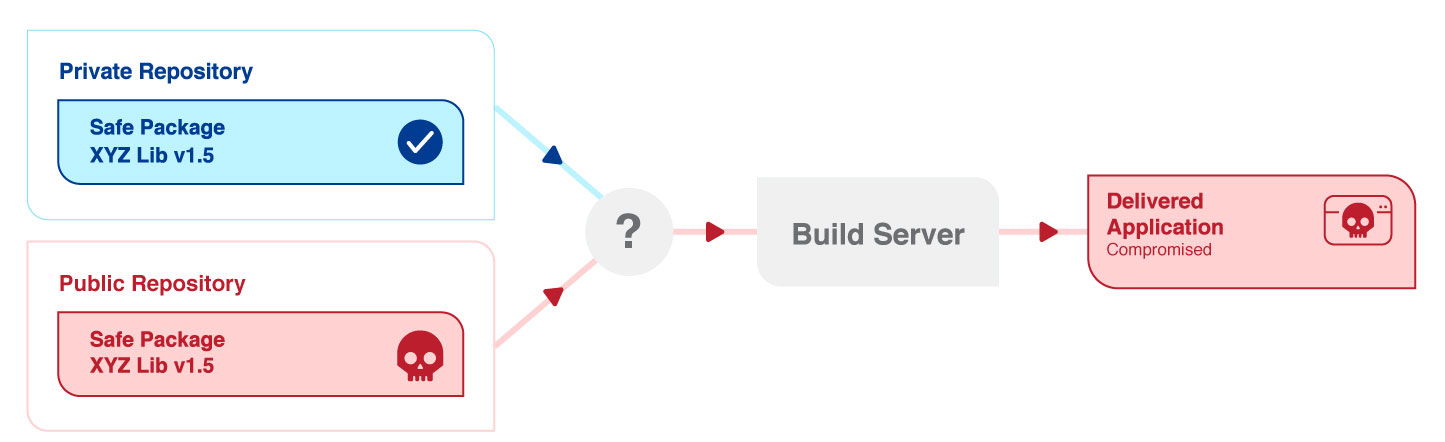
Another supply chain attack vector, “Dependency Confusion”, was announced by security researcher Alex Birsan in early 2021. The Dependency Confusion attack involves a deliberate confusion of the package manager whereby malicious artifacts are placed in public repositories, and the package manager is misled into downloading and installing the affected code.
Open-source libraries are essentially collections of generally useful utility code that are openly available via these “public” repositories. Open-source software is found in the vast majority of software applications. Hence, an organization’s build tools must be able to pull code from both the “private” (i.e. repositories which are only accessible to the organization that is producing the application) and “public” repositories. In the cases of Dependency Confusion, the attacker merely has to register a package with the same name in a public repository as a package in a private repository. This will lead to a potential for the attacker’s package to be “pulled” by the build tool instead of the intended internal package. In most cases, the malicious package is named with a higher version number, which results in the build tool pulling the attacker’s library instead of the intended internal library with a lower version number. This attack vector has been demonstrated to be surprisingly efficacious, given the complexity of modern software applications and their strong reliance on open-source code. Are you keen to know more? Keep a look out for our next newsletter in which we will delve deeper into Dependency Confusion attacks.

The extensive reliance on third-party code by organizations worldwide, which could easily expose your applications to vulnerable and risky components, simply make up the reality of cloud native software supply chain. The consequence of this connectivity is that attackers are provided with plenty of options for targeting legitimate software through third party providers and embedding themselves in the development process. While the dangers of Supply Chain attacks are at an all-time high, they will only evolve with time. Organizations should be adaptive with their security practices to promptly detect, identify, and mitigate these attacks.

About softScheck
softScheck is an experienced cyber security consultancy firm that can help you with the prevention of Dependency Confusion through our service offerings. We perform IT Security Audits to inspect how your company manages your repositories and your policies on the retrieval or use of public packages, with the aim of compliance with security best practices. We also provide Web Penetration Tests to ensure your list of internal libraries and packages are not publicly exposed and provide recommendations to reduce any unnecessary exposure.
Please contact our friendly BD Director at [email protected] for a more in-depth discussion on how we can help your organization mitigate against Dependency Confusion and improve your security posture.




