IoT Security Testing
What is IoT Testing?
The Internet of Things (IoT) encompasses all products that are connected to the internet or to each other. Many manufacturers have no prior experience with networked devices and are bound to overlook software security design. With over 50 billion IoT devices connected to the internet, the number of security risks that consumers and businesses are prone to facing will increase exponentially.
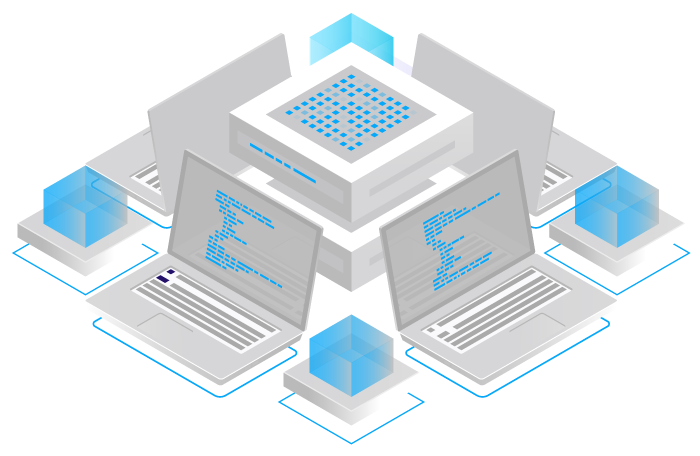
How does IoT work?
IoT Penetration Testing (a.k.a. IoT Pentest, IoT VAPT, IoT Pen Testing) tests the security hygiene of an IoT device. It identifies if a device can be altered to complete an unauthorised task, whether the authentication requirement can be easily bypassed or if vulnerabilities could be abused.
An IoT environment mostly includes the following components: Network, Applications, Firmware, Encryption and Hardware. The security testing process for IoT is inherently more complicated because there is more hardware, software, and communication protocols involved. Given the variability of IoT devices, every pen test approach is unique and calls for creativity to cover all possible bases of attacks on a device.
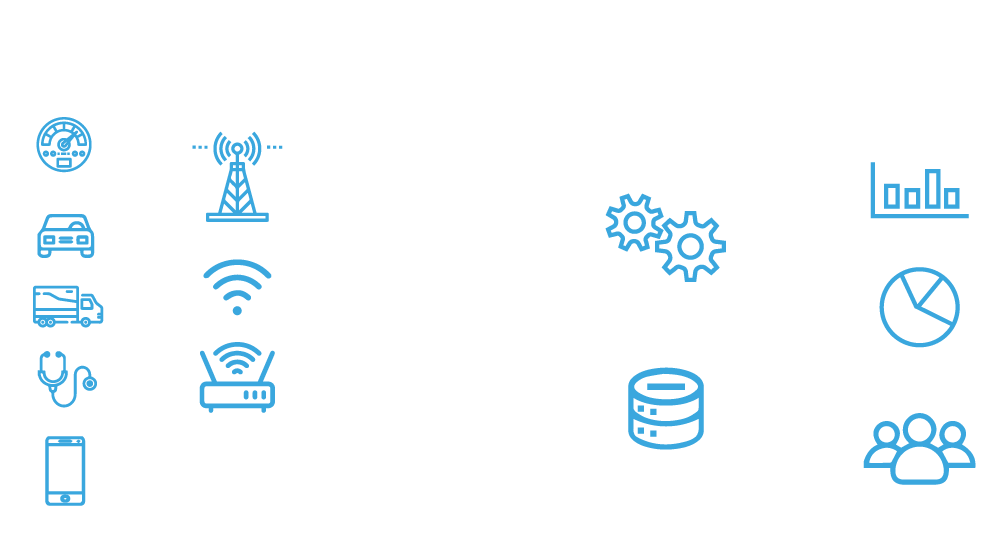
Objective of IoT Pen Testing Assessment
Approach & Methodology
The IoT Penetration Testing methodology is based upon industry standards, including but not limited to the OWASP Internet of Things. The OWASP Top 10 for IoT provides a good baseline for penetration testing, it includes:
Trusted IoT Penetration Testing Partner
softScheck is well-versed in IoT security and penetration testing for public and private corporations across various industries and sizes. We are fully equipped with the expertise to conduct IoT security testing for the most complex systems. Our team, based out of Singapore, holds client satisfaction above all and we aim to build trust as your cybersecurity partner.
We’re a CREST accredited penetration testing provider, upholding the mark of excellence and a demonstrable level of quality for cybersecurity services through appropriate policies, processes, and procedures for companies in Singapore and worldwide. Speak to us to ramp up your IoT security today.