What are supply chain attacks?

When the topic of a cyberattack or data breach comes to mind, it is most often that people imagine a direct assault – a bad actor looking for vulnerabilities in the software and systems of your organization to find a way in. While this type of attack is commonplace and has garnered considerable attention, there are other emerging attack vectors that businesses should also be aware of. Our series of softScheck newsletters will detail some of these attacks in the coming months, so keep your eyes peeled!
The expanding connectivity between businesses in recent times have prompted an increasing reliance on tools from vendors and suppliers. The growing dependence of businesses on these external entities greatly complicates the cybersecurity landscape and gives rise to a new category of threat – Supply Chain attacks. Beyond dns attacks and other direct security threats, the emergence of this new form of attack could potentially put your organization in an even more dangerous position than ever before. This article will shine light on Supply Chain attacks and the various methods (to look out for) in which malicious actors may compromise data security. We will also discuss two scenarios in which the ripple effect of these Supply Chain attacks have culminated in widespread consequences that affected many businesses.
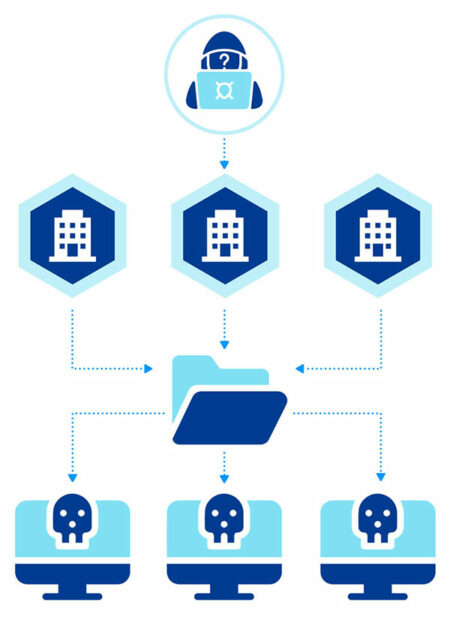
An attack strategy which targets your business through the vulnerabilities in your supply chain is known as a Supply Chain attack. This type of attack features a typical connection between vulnerable areas in an organization to external vendors with poor security practices. The data breach to an organization is rendered possible through these third-party vendors who require access to sensitive data for integration with internal systems. Hence, a vendor’s compromised security systems usually also mean the breach of this shared pool of data. A single vendor often stores sensitive data for multiple clients and a single Supply Chain attack can result in the intellectual property breach of numerous organizations.

The main components which are targeted in software Supply Chain attacks are commonly the source code, update mechanism, or build processes of vendor software. Any of the following attack vectors can be used by bad actors to penetrate a victim organization and potentially lead to a compromise of data security:
- Vulnerable Software Development Tools or Infrastructure. The tools for building software applications are leveraged by hackers to introduce security weaknesses early in the development process, which could be even before the process is used for the creation of an application.
- Pre-Installed Malware on Devices. Hackers can plant malware on several devices such as phones, Universal Serial Bus (USB) drives, cameras, and other mobile devices, such that malicious code is introduced when these devices are connected to the targeted system or network.
- Stolen Certificates. Certificates which are used to vouch for the legitimacy or safety of an organization’s product can be stolen by hackers to peddle malicious code under the guise of that organization’s certificate.
- Malicious Code Hidden in Component Firmware. Digital hardware is controlled by firmware which helps it to run smoothly and interface with users and other systems alike. Hackers may obtain access to a target system or network by including malicious code in the firmware.
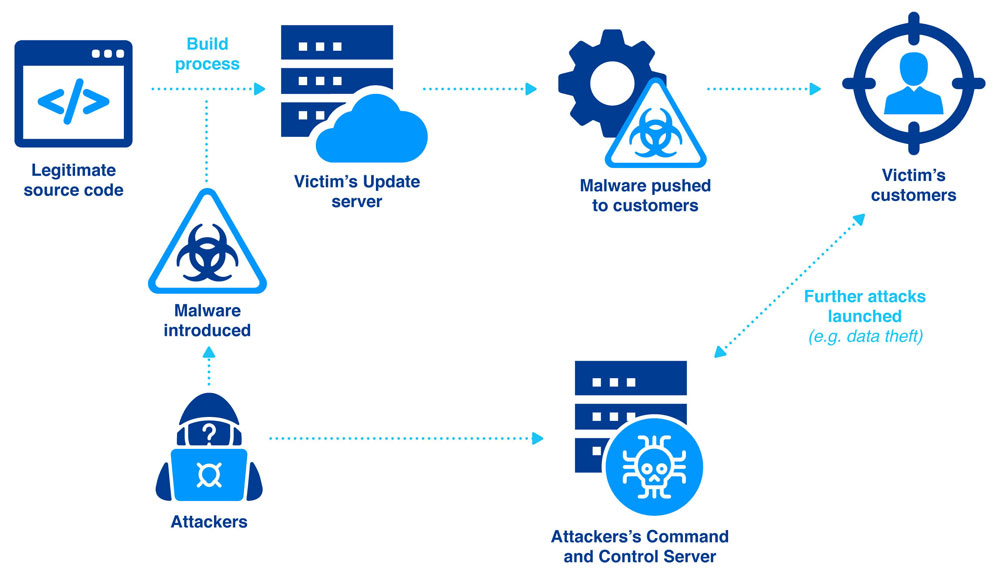

These real-life scenarios demonstrate the far-reaching ramifications of a Supply Chain attack:

The affected IT security company, FireEye, initially detected the attack around December 8, 2020. While FireEye warned the public against the usage of its security products, they had denied that zero-day vulnerabilities had been identified. The malicious actors managed to manipulate an update of the network monitoring platform Orion of SolarWinds Inc. to install a backdoor (two have already been published to date) in approximately 18,000 of the estimated 300,000 customer systems. This backdoor was then used by the hackers to install even more malware to spy on the victim organizations and even affected the upper echelons of the US Government, including the Department of Homeland Security and Treasury Department. This massive Supply Chain attack comprised of FireEye clients from not only the public sector in USA and Great Britain, but also the world’s largest companies in various sectors (such as defense, technology, banking, consulting, pharmaceutical/chemical, telecommunications, and raw materials) in North America, the Middle East, Asia, Europe, Germany, and all the states in the European Union. SolarWinds had taken the world by storm in an unprecedented Supply Chain attack which has left numerous corporations reeling in the vulnerable aftermath in the many months that followed.

Zero-day vulnerabilities, security flaws that have just been discovered and which a patch does not essentially exist, are one of the most difficult to protect against. The Microsoft Exchange attack involved the discovery of a series of zero-day vulnerabilities in which the perpetrators could chain together to break into any of the internet-accessible Exchange servers. This resulted in their ability to steal all the emails and files which were stored on these servers. Depending on how the damage is measured for this Supply Chain attack, these vulnerabilities were known to have affected 250 000 Exchange servers, of which at least 30 000 appeared to have been compromised.

These two scenarios of Supply Chain attacks happened on such a massive scale with extensive consequences. Although they are believed to be in no way connected to the same (possibly state-sponsored?) threat actors, the prevailing concern remains – could an over-reliance on connected applications or services by external parties compromise your enterprise networks? Where does this leave your organization?
The ability of attackers to infiltrate organizations by targeting their suppliers only means that businesses must become much more formidable defenders. It is imperative to develop your organization’s ability to detect things which have gone awry in your environments and respond early in the attack lifecycle when there is still a decent chance to minimize any damages. This will require the right tools, imaginative processes, and a cadre of well-trained professionals.

About softScheck
softScheck is an experienced cyber security consultancy firm that can help you with the prevention of Dependency Confusion through our service offerings. We perform IT Security Audits to inspect how your company manages your repositories and your policies on the retrieval or use of public packages, with the aim of compliance with security best practices. We also provide Web Penetration Tests to ensure your list of internal libraries and packages are not publicly exposed and provide recommendations to reduce any unnecessary exposure.
Please contact our friendly BD Director at [email protected] for a more in-depth discussion on how we can help your organization mitigate against Dependency Confusion and improve your security posture.




